SSH Public Key infrastructure does not typically use certificates or certificate authorities, it pins the public keys directly, with a trust model based on TOFO (trust-on-first-use). When you first connect to an SSH server, it asks you to trust the host key and displays a visual representation of the key, like this
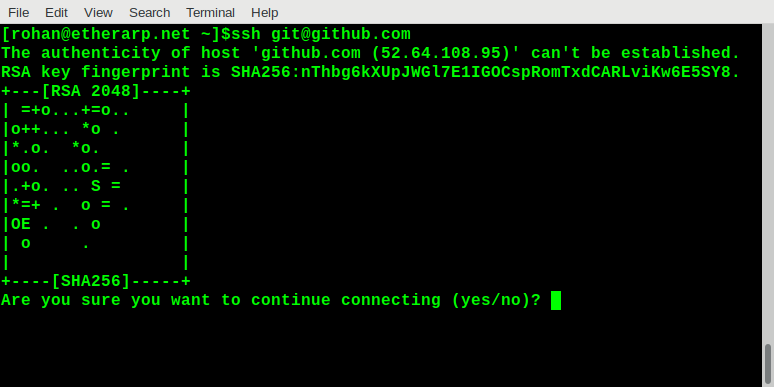
The public key cryptography SSH uses is very similar to what's used with TLS/SSL so it should be straightforward to generate the random art for an HTTPS server. The main difference with TLS is that certificates are verified rather than keys; certificates are generated from keys. So if a website you trust starts showing a certificate error, it will be useful to know whether or not the underlying key has changed.
My script is pretty simple and has the following steps:
openssl s_clientconnects to the server and verifies it against a CA bundle (this is optional). The server certificate is printedopenssl x509extracts the public key from the certificatessh-keygen -viconverts the public key from the standard TLS format-m PKCS8to the SSH formatssh-keygen -vlprints the random art
Trying it out
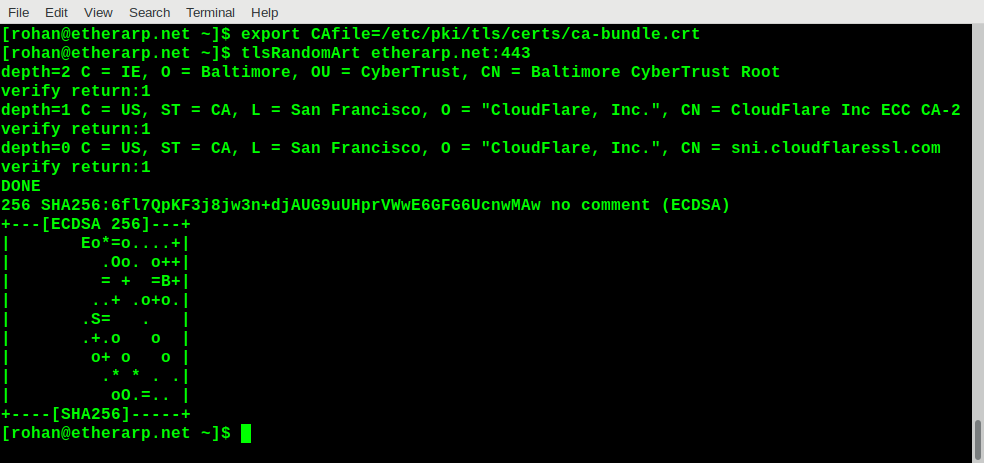
Final notes
The output is based on the public/private key pair used to generate the certificate signing request, not the certificate itself. So two certificates will give the same output even if they have a totally different common name and are signed by a completely different certificate authority.
This script could be used to check if a server is still secured with the same public key after its certificate has changed, or to detect man-in-the-middle attacks