The Ubiquti Edgerouter Lite has an iptables based firewall. For each firewall rule (and named set of ules) there is a is an option to enable LOG.
Unsolicited traffic to tcp ports, especially ssh, telnet is very common and so our log gets quite large, rather quickly. On a device with limited storage like the EdgeRouter, a barrage of blocked traffic may rapidly fill memory and crash the device.
How to do it:
We use iptables-save to get the current iptables rules. We then use sed to find/replace. We replace -j LOG with -m limit --limit 3/min -j LOG, so that the logging action is done at a maximum rate of 3/min.
$ sudo iptables-restore< <(sudo iptables-save | sed s/'-j LOG'/'-m limit --limit 3\/min -j LOG'/)
The number of 3/min is kind of conservative, so you may want to adjust it to your needs.
Running the command at boot
To run the command at boot, all we need to do is create a script in /config/scripts/post-config.d
Fine tuning
Because now, your default target is limited to 3 logs per minute (on average). It's a good idea to create some redundant rules.
Even though your default target is DROP, we should also add our own redundant rules. By 'redundant' I mean adding rules for things that would have otherwise been blocked by the default action.
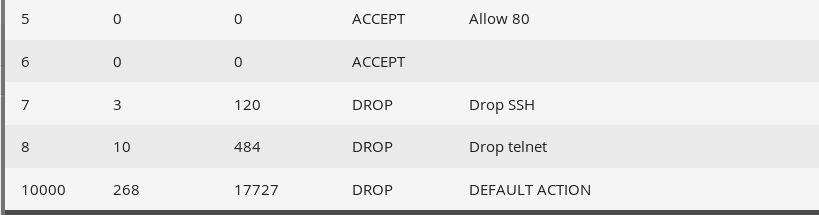
Why is this useful? Because each rule in iptables has a hit counter, which we can view with iptables --list --numeric .
By adding rules like "block ssh", "block dns", "block ipset chinanet" we can get the numbers of how ssh or dns traffic we receive and what proportion it is of the overall traffic. This adds much more clarity than just seeing "blocked x number of packets".
Furthermore, on a rule by rule basis, we can override the rate limits and set a custom log prefix.
Later, we will look at using Amazon S3 to keep logs of the EdgeRouter's status