This post covers how to configure Github based login for the Caddy webserver. This allows single sign on using Oauth2. The Caddy plugins http.jwt and http.login are required.
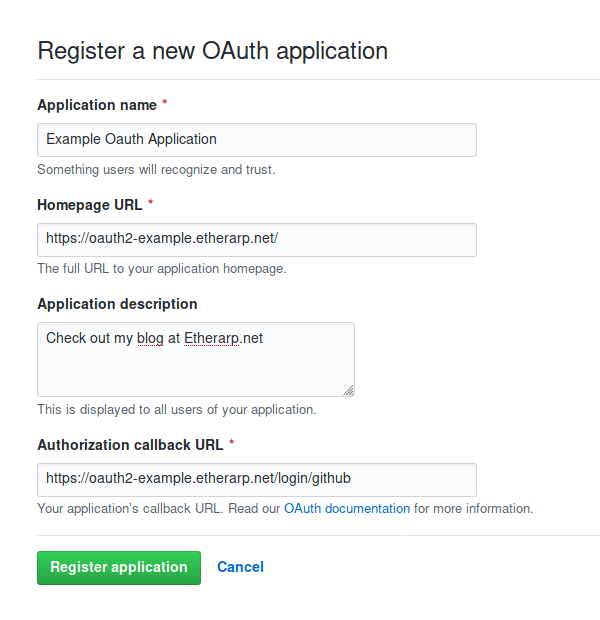
Create an Oauth2 App in Github
Log into your Github account and open Developer Settings.
Create a new Oauth2 App, set https://<domain>/login/github as the Authorization Callback URL
Install Caddy
Using Oauth2 requires the http.login and http.jwt plugins, which are not included by default. There are a number of ways to build Caddy - I used the Dockerfile below. To build, run the following command docker build . -t local/caddy. You will need a Caddyfile and index.html in your working directory.
Once Caddy has been built, it can be started using docker-compose.
Configure Caddy
This is the Caddyfile. All requests to / are redirected to /login. On successful Oauth2 verification, the user is redirected to /internal/index.html. The sub statement specifies the authorized Github accounts (by username)
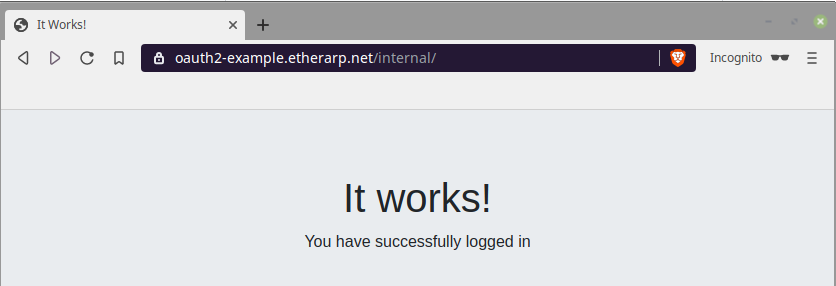
Trying it out
In a private window, I open up my site, and as expected, it redirects to the login page
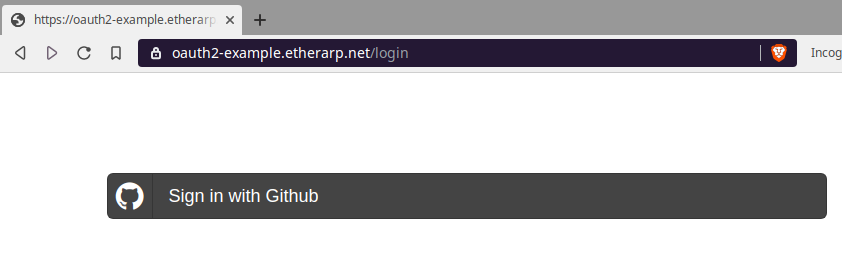
The sign in link points to a login page on the Github.com domain
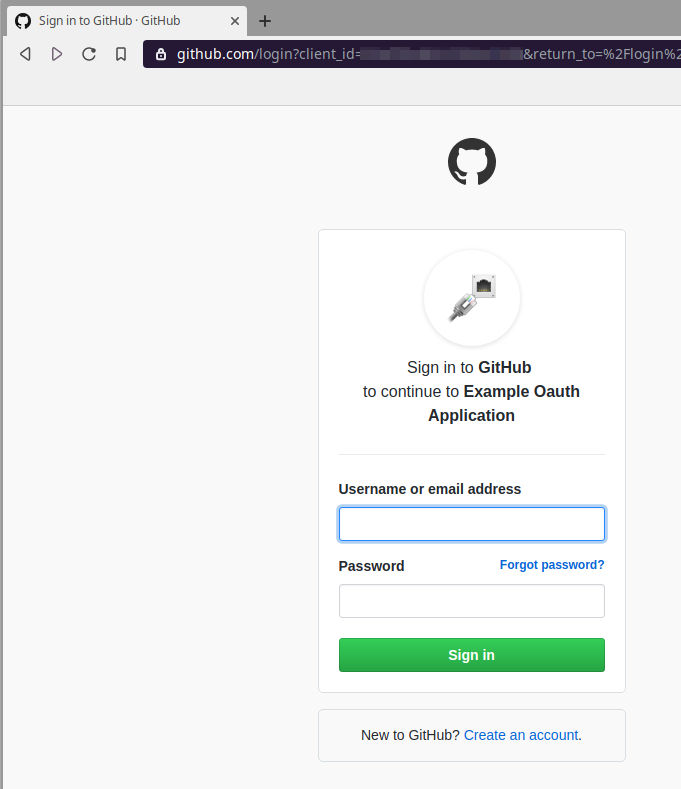
The first time you log in, you will have to associate the Oauth2 App with your Github account; only associate your account with sites you consider trustworthy!
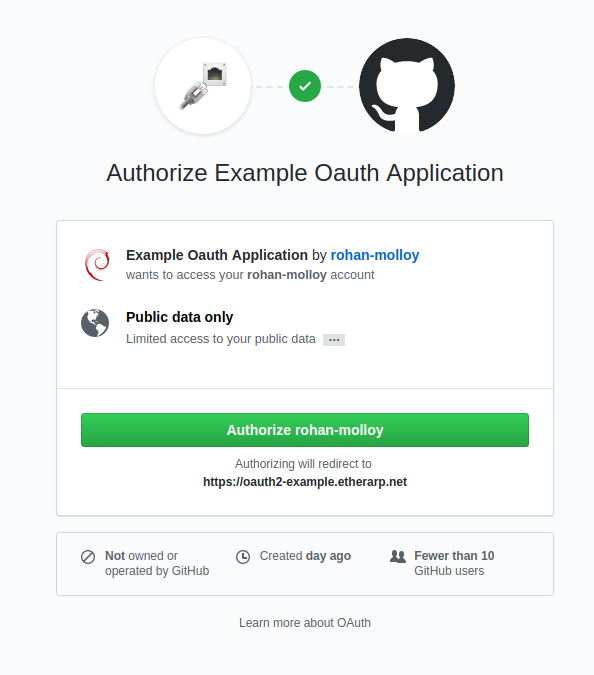
Upon authorization, you will be redirected to the site's internal area.